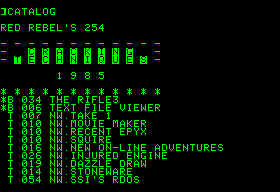
L'année suivante: 1985.
On ne change pas une formule gagnante.
Cette série fut à l'origine des initiatives de
disks de
cracking qui suivirent.
Les cours de déplombage en furent aussi les
héritiers.
A noter que je n'ai plus trouvé de publicité dans
la presse
à partir du numéro de 1984. Peut-être
que les éditeurs n'en avaient plus besoin ou alors que
l'image du sympatique pirate façon " Wargames "
avait du plomb dans l'aile... Il n'est pas impossible non plus que
certains magazines se soient mis à boycotter les productions
portant un drapeau à tête de mort.
On remarquera avec malice sur un des écrans ci-dessous le
warning concernant l'usage légal de ce disk. No comment
:-))))
Comme les précédants numéros,
plusieurs articles sont toujours minimalistes.
On voit néanmoins se détacher du lot le
déplombeur The Disk Jockey
qui essaie de s'impliquer
d'avantage et a produit ici une bonne partie des fichiers.
On notera pas exemple son article sur le RDOS de
la
société américaine SSI.
The Disk Jockey marcha sur les
pas de son
prédécesseur Krakowicz
et finit par la suite
à remplir des disks d'explications à lui tout
seul.
Ma disquette provient d'un achat sur ebay (avant l'arrêt de
ma collection suite aux problèmes postaux).
Il s'agit d'un original. Le .dsk est donc certifié
0% graffiti
supplémentaire.

|
DOS 3.3
|
Download Original disk: Cracking
Techniques 1985
(gzipped)
|
Sommaire
| Lien
|
Information
|
 |
01) CRACKING TOOLS.
|
 |
02) TAKE 1.
|
 |
03) MOVIE MAKER.
|
 |
04) RECENT EPYX.
|
 |
05) SQUIRE.
|
 |
06) NEW ON-LINE ADVENTURES.
|
 |
07) INJURED ENGINE.
|
 |
08) DAZZLE DRAW.
|
 |
09) STONEWARE.
|
 |
10) SSI'S RDOS.
|
 |
11) SAMMY LIGHTFOOT.
|
 |
12) MARIO BROS.
|
 |
13) 'THE QUEST' CRACK.
|
 |
14) PEACHTREE.
|
 |
15) STANDING STONES.
|
 |
16) DESIGNWARE.
|
 |
17) CRACK MURDER BY THE DOZEN.
|
 |
18) EASY COM/EASY GO.
|
 |
19) ADVENTURE WRITER.
|
 |
20) PATTERN MAKER.
|
 |
21) BANK STREET WRITER //C.
|
 |
22) CRACK MICKEY'S SPACE ADV.
|
 |
23) KRACK PANDORAS BOX.
|
 |
24) SENSIBLE SPELLER PRO.
|
 |
25) KRACK MICRO LEAGUE.
|
 |
26) CALCULUS TOOL KIT.
|
 |
27) THE MISSING RING.
|
 |
28) CAVERNS OF FREITAG.
|
 |
29) COVETED MIRROR.
|
 |
30) CRACK TREASURE HUNTER.
|
01) CRACKING TOOLS.
MSG LEFT BY: RED REBEL
THE FOLLOWING TOOLS SHOULD BE IN YOUR
ARSENAL FOR CRACKING:
'BENEATH APPLE DOS' QUALITY SOFTWARE
'BENEATH APPLE PRO DOS QUALITY SOFTWARE
'BAG OF
TRICKS'
QUALITY SOFTWARE
'WHAT'S WHERE IN THE APPLE' MICRO INK
'APPLE MONITORS PEELED APPLE COMPUTER
INTEGER
CARD
APPLE COMPUTER
LANGUAGE
CARD
APPLE COMPUTER
MASTERDISK
MASTERWORKS SOFTWARE
MASTER
DOS
MASTERWORKS SOFTWARE
D-A-R-K
MICROSEEDS
NIBBLES AWAY COMPUTER
APPLICATIONS
LOCKSMITH
5.0
OMEGA
MR.
FIXIT
OMEGA
INSPECTOR
OMEGA
WATSON
OMEGA
COPY ][ PLUS CENTRAL POINT
SOFTWARE
BEAGLE BROTHERS SOFTWARE FROM SAME
ANY OF THE VARIOUS NON MASKABLE (NMI)
INTERRUPT CARDS SUCH AS:
CRACK-SHOT,REPLAY II, WILDCARD
GOOD BOOKS ON MACHINE LANGUAGE BY:
ROGER WAGNER & RANDY
HYDE
CRACKING TECHNIQUES '83 PIRATES HARBOR
CRACKING TECHNIQUES '84 PIRATES HARBOR
KRAKING-DISK JOCKEY
PIRATES HARBOR
CRACKING-APPLE BANDIT
-THE BURGLAR PIRATES HARBOR
Any of thes products may be obtained
from PIRATES HARBOR if you can not
get them from your local dealer.
KEEP ON CRACKING!!!
>>> RED REBEL <<<
Retour sommaire
02) TAKE 1.
Kraking Take 1 from Baudville Software.
By the Disk Jockey.
Requirements:
-Apple II, II+ or //e with 64K of RAM.
-At least one disk drive with DOS 3.3.
-A sector editor.
-Take 1 from Baudville Software.
1) Boot normal DOS 3.3 and disable the
DOS error checking routines by typing:
]CALL-151
*B942:18
*3D0G
2) Run COPYA and modify it slightly to
continue copying on unreadable sectors
by typing:
]RUN COPYA
CTRL C (after the drive stops)
]CALL-151
*3A1:18
*3D0G
]70
(delete line 70)
]RUN
3) Copy the original Take 1 disk to a
blank disk.
4) Run your favorite sector editor and
make the following changes to the COPYA
version of Take 1:
Track 0, Sector 6, Byte $16
Change from $D0 F7
to $EA EA
Track 0, Sector $F, Byte $08
Change from $D0 F7
to $EA EA
5) Write the sectors back out.
And you're all done!
-The Disk Jockey-
Retour sommaire
03) MOVIE MAKER.
Deprotecting Movie Maker from
Interactive Picture Systems. By the
Disk Jockey.
Requirements:
-Apple II, II+.
-64K of RAM (required by program).
-some means to reset into the monitor.
-COPYB
-A sector editor.
1) Boot the original Movie Maker disk,
and after the APPLESOFT cursor appears,
reset into the monitor.
2) Move the RWTS down to $8000 by
typing:
*8000<B700.BFFFM
3) Boot a normal DOS slave disk and
defeat the normal DOS error checking
routine at $B942 by typing:
]CALL-151
*B942:18
4) Run COPYB by typing:
*RUN COPYB
5) Respond to COPYB's parameter
questions as follows:
starting track = 0
ending track = 16
Defeat DOS error checking = Yes
Continue reading on errors = Yes
6) Copy side one of the Movie Maker
disk to a blank disk.
7) Reboot normal DOS and run COPYA by
typing:
]RUN COPYA
8) After the drive stops, you must
change COPYA so it only copies tracks
$11 to $22. Do this by typing:
CTRL
C
(exits into BASIC)
]CALL-151
*2B0:A9 10 8D D1 02 8D D2 02 60
*2DC:20 B0 02 A9 FF 9D D3 02 CA 10 F8
*3D0G
]70
]DEL 246,250
]RUN
9) Re-boot normal DOS and run your
favorite sector editor.
10) Make these byte changes to the
copied Movie Maker disk using your
sector editor:
Track 0, sector 0,
byte $4A from $AA to $D5
byte $53 from $D5 to $AA
byte $5D from $AB to $96
byte $88 from $AA to $D5
byte $91 from $D5 to $AA
byte $9B from $EB to $AD
Track 0, sector 3,
byte $1A from $AA to $D5
byte $23 from $D5 to $AA
byte $2D from $AB to $96
byte $57 from $AA to $D5
byte $60 from $D5 to $AA
byte $6A from $EB to $AD
11) Write the sector back out to disk.
Your all done!
-The Disk Jockey-
Retour sommaire
04) RECENT EPYX.
Deprotecting Robots of Dawn and Pitstop
II from Epyx Software. By the Disk
Jockey.
Requirements:
-Apple II, II+, //e, or //c.
-A sector editor.
-COPYA from the DOS 3.3 System Master.
-Master Create from the DOS 3.3 System
Master (Pitstop II only).
-A blank disk.
-Robot Dawn or Pitstop II from Epyx
Software.
ROBOTS OF DAWN:
---------------
1) Boot normal DOS 3.3 and enter the
monitor by typing:
]CALL-151
2) Defeat the DOS error checking by
typing:
*B942:18
3) Put your DOS 3.3 System Master in a
drive and type:
*RUN COPYA
4) Copy the Robots of Dawn original
disk to a blank disk.
5) Reboot normal DOS 3.3 and run your
favorite sector editor.
6) Make the following change to your
COPYA copy of Robots of Dawn:
Track 0, sector 5
change byte $AC from $38 to $18
7) Write the sector back out to your
COPYA copy of Robots of Dawn.
Pitstop II:
----------
1) Boot normal DOS 3.3 and enter the
monitor by typing:
]CALL-151
2) Defeat the DOS error checking by
typing:
*B942:18
3) Put your DOS 3.3 System Master in a
drive and type:
*RUN COPYA
4) Copy the original Pitstop II disk to
a blank disk.
5) Reboot normal DOS 3.3 and make sure
your DOS 3.3 System Master is in a
drive.
6) Run Master Create by typing:
]BRUN MASTER CREATE
7) Put the COPYA Pitstop II disk in
drive one and specify "BOOT" as the
hello program name you want and update
the COPYA Pitstop II with DOS 3.3.
8) Run your favorite sector editor and
make to following change to your COPYA
copy of Pitstop II:
Track 0, sector 5
byte $42 from $06 to $34.
9) Write the sector back out to the COPYA Pitstop II.
Now both programs are deprotected.
-the Disk Jockey-
Retour sommaire
05) SQUIRE.
Deprotecting Squire from Blue Chip
software. By the Disk Jockey.
Requirements:
-Apple II, II+, //e or //c.
-At least one DOS 3.3 disk drive.
-FID from the DOS 3.3 System Master.
-2 blank disks.
-Squire from Blue Chip software.
Squire uses track 35 (one past the
norm) for its protection. Here is
how to defeat it:
1) Boot your original Squire disk and
immediately press CTRL C. This will
cause Squire to exit to BASIC just
after DOS is loaded.
2) Put a blank disk in a drive and
type:
]INIT ENTRA
3) Put your DOS 3.3 System Master in a
drive and type:
]BRUN FID
4) Using option 1, copy all the files
from the original Squire disk to the
newly intialized blank disk (use the
"=" wildcard command from FID).
5) Make sure your backup copy of Squire
is in a drive and exit from FID to
BASIC (option 9) and BLOAD the file CON
by typing:
]BLOAD CON
6) Enter the monitor and make these
changes to the CON program by typing:
]CALL-151
*403B:EA EA EA EA
*4064:60
*40A0:A9 11
*40B6:EA EA EA
*40C0:EA EA EA
*40CA:EA EA EA
7) Save the modified CON file to your
backup copy of Squire by typing:
*BSAVE CON,A$4000,L$140
8) Boot side 2 of the Squire disk.
9) When the BASIC prompt has appeared,
put a second blank disk in the drive
and type:
]INIT HELLO
10) After the disk is initialize, put
your DOS 3.3 System Master in a drive
and type:
]BRUN FID
11) Copy all the files from the second
side of the Squire disk to your newly
initialized disk using option 1.
Squire is now deprotected and may
copied as desired.
-the Disk Jockey-
Retour sommaire
06) NEW ON-LINE ADVENTURES.
Deprotecting Winnie the Pooh and
Mickey's Space Adventure from Sierra
On-line. By the Disk Jockey.
Requirements:
-Apple II, II+, //e or //c.
-At least one DOS 3.3 disk drive.
-COPYA from the DOS 3.3 System Master.
-A sector editor.
-Several blank disks.
-Winnie the Pooh and/or Mickey's Space
Adventure from Sierra On-line.
These two new On-line releases are
absolutely COPYAable with no
modifications. Of course your COPYA
copies will not work because of a track
0 nibble count. It is easy to find the
nibble count and defeat it though...
What I did was to make copies of the
boot side of each of the adventures
(only the boot side is protected), and
then booted them. I watched and
listened to the disks load. Shortly
after the first title page appeared, I
heard the drive head seek to track 0
and sit there for a second. Then BOOM!
The program bombed because the nibble
counted track 0 was not preserved in
the COPYA copy.
So I let the COPYA copy boot a few
times and got a feel for where the
nibble count occurred during the boot.
Then, using a Replay II card, I pressed
the Replay button when I heard the
track 0 nibble count. I had to be quick
about it, must press the button before
the program bombs. It took a few times
of practice...
After I press the Replay II card
button, I entered the Replay monitor
and checked the program counter. The
program counter is the address the
program was running at when
interrupted. For Winnie the Pooh, the
program counter was between $A17 and
$A70. For Mickey's Space Adventure, the
program counter was between $1527 and
$1580. So next I reseted into the
monitor and examined the code at page
$0A (for Winnie, page $15 for Mickey).
It was pretty obvious that it was a
nibble count where the program was
running. It was also pretty obvious
that the starting address of the nibble
counts was $A17 and $1527 for Winnie
and Mickey, respectively. The starting
address was easy to determine since all
the code before those addresses were
zeros for about half a page.
Now that I knew where the nibble count
lived, it was just a matter of finding
where is was being called from and
defeating the call on the disk. This
required using the Inspector's Locate
command to search the disk for a JSR
$A17 for Winnie, and a JSR $1527 for
Mickey. After finding the calls, all
was left was to NOP them (replace the
JSR's with NOPs or No Operating
Instruction)!
In cookbook format, here are the
procedures for deprotection Winnie the
Pooh and Mickey's Space Adventure:
1) Boot normal DOS 3.3 and run COPYA
from your DOS 3.3 System Master by
typing:
]RUN COPYA
2) Copy all the sides of either (or
both) Winnie the Pooh and Mickey's
Space Adventure.
3) Run your favorite sector editor and
make the following sector changes to
your COPYA copy:
Winnie the Pooh
---------------
Track $F, sector $E, side 1
byte $3B from 20 17 0A to EA EA EA
Track $17, sector $D, side 1
byte $3B from 20 17 0A to EA EA EA
MICKEY'S SPACE ADVENTURE
------------------------
Track $18, sector $E, side 1
byte $18 from 20 27 15 to EA EA EA
4) Write the sectors back out to the
COPYA copy.
And you're all done.
-the Disk Jockey-
Retour sommaire
07) INJURED ENGINE.
Deprotecting Injured Engine from Imagic.
By the Disk Jockey.
Requirements:
-Apple II, II+, //e or //c with at
least one disk drive.
-COPYA from the DOS 3.3 System Master
disk.
-A sector editor.
-2 blank disk.
-Injured Engine from Imagic.
Injured Engine is not only a simulation
but also a game. You can also be
presented with 5 engine problems that
you have to correct using a minimum
amount of time and money. And there is
complete descriptions of each part of
the engine, if you don't understand a
particular part or function.
Injured Engine used only the RWTS
portion of DOS to load the program.
This is evident from the lack of an
APPLESOFT cursor upon booting the disk.
To confirm this, I reseted into the
monitor during the load and examined
$B700-BFFF. There was a pretty standard
RWTS there.
And as it turns out, most of the disk
in unprotected. Only track 6 was
unreadable by normal DOS, and we'll
find out why in a minute.
My first action was to trace the boot.
Pretty much a standard boot. After the
disk controller card loaded track 0,
sector 0 into $800-8FF, the routine
there loaded in RWTS and jumped to
$B700. A few instructions from $B700
there was a JSR $BEAF (jump subroutine
at $BEAF.
Following this routine lead me to a JSR
$B500 (jump subroutine at $B500). Now
this routine was suspicious. It checked
for normal DOS address and data
markers. Remember that these markers
tell DOS what track and sector it is
trying to read (address markers), and
where the data actually starts on the
disk for that sector (data markers). A
pretty standard protection is to change
these markers from a normal DOS format,
so copy programs can not accurately
tell where the data actually is on a
track.
OK, but why was there this routine that
checked for NORMAL DOS address and data
markers? Shouldn't it be checking for
some perverted format on that
unreadable track 6? After all, RWTS has
its own routines to check for normal
data and address markers. Why not use
those?
Well, the answer is they are checking
for normal DOS address and data markers
on track 5 and track 5.5. Why are they
doing that, and why does that make
track 6 unreadable?
To understand this we must understand
the 35 track, standard Apple disk
drive. A pretty common trick is to use
half tracks in protection schemes. But
you can not get 70 tracks by using
track 1, 1.5, 2, 2.5, etc. The reason
is that the drive head on the Apple can
not WRITE with that much precision. If
you try to write to track 2 and then
track 2.5, you get "track bleeding",
and get very unpredictable results.
So if you use half tracks you still end
up with 35 tracks, but on half track
increments (1.5, 2.5, 3.5, etc.). If
you want to skip back to whole tracks,
you have skip a track, like using track
6.5 and then track 8.0. This is because
track 7 or 7.5 is too close to tracks
6.5 or 8, respectively.
But if adjacent half tracks were
WRITTEN reliably (with very accurate
drive equipment) you could READ them
back reliable with a standard Apple
drive. So if you had the drive
equipment, you could produce a disk
that used adjacent half tracks (i.e.
6.5, 7, 7.5, 8, ect.).
This is what Imagic has done. They used
some very accurate drive equipment to
reliably write tracks 5 and 5.5 (but
not track 6, hence wiping it out). Then
their protection scheme just reads
these tracks back, checking that they
are readable and in the correct (normal
DOS) format.
This is what the routine at $B500 does.
It reads tracks 5 and 5.5, and if they
are not BOTH readable, it reboots. If
they are readable, it continues along
and loads the title page.
This is an uncopyable protection
scheme! Regardless of the copy program
you use, you can not make a copy of the
original Injured Engine disk since your
standard Apple drives will not write
tracks 5 AND 5.5 reliable.
But fortuneately, we can defeat the
routine that ultimately decides if both
tracks 5 and 5.5 were read correctly.
All we have to do is to NOP three bytes
at $B5B3 (NOP is the 6502 instruction
code that represents No OPerating
instruction). This defeats the whole
prtection scheme. By the way, there is
no valid data on tracks 5, 5.5, or
track 6. The routine at $B500 only
checks to see if tracks 5 and 5.5 are
readable in normal DOS format.
Now we must just find this code on the
disk, and use our sector editor to
change it. I used the disk search
utility in the Inspector to find the
code. It is on track 0, sector 5, bytes
$B3 to $B5.
The only thing left to think about is
how to copy the whole disk except track
6. Many disk utilties will do this for
you (like Locksmith 5.0 Fastcopy), but
I will explain how to do it with COPYA,
since everyone has COPYA:
Here is the Cookbook steps to
unprotecting Injured Engine:
1) Boot your normal DOS 3.3 System
Master.
2) Run COPYA by typing:
]RUN COPYA
3) After COPYA is loaded and asking for
slot and drive specifications, press:
CTRL C
4) You should now be in BASIC. We have
to defeat the UNABLE TO READ error.
Type the following:
]CALL-151
*3A1:18
*3D0G
5) Now delete line 5 of COPYA and run
the program by typing:
]5
]RUN
6) Copy the original Injured Engine
disk to a blank disk. Note that your
drive will spit and spudder on track 6.
Just ignore this and let the copy
finish.
7) Reboot your DOS 3.3 System Master
and type:
]RUN COPYA
8) Now copy side 2 of Injured Engine to
a blank disk (note: side 2 is
unprotected).
9). After the copy is done, run your
sector editor and make the following
sector changes to side 1 of your COPYA
Injured Engine:
side 1, track0, sector 5, byte $B3-B5
from E8 F0 3C
to EA EA EA
10) Don't forget to write the sector
back out to your COPYA Injured Engine.
And you're all done!
-The Disk Jockey-
Retour sommaire
08) DAZZLE DRAW.
Deprotecting Dazzle Draw from
Broderbund Software. By the Disk
Jockey.
Requirements:
-Apple //e or //c with 128K.
-COPYA from the DOS 3.3 System Master.
-1 blank INITialized disk.
-1 blank disk.
-Dazzle Draw from Broderbund Software.
-Lots of Patience.
Lets face it, some companies just
protect their software better than
others. When I think of good protection
schemes, publishers like Sirius (RIP),
Electronic Arts and Broderbund come to
mind. Usually deprotecting these
programs is very difficult and requires
a great deal of time and ingenuity. But
what is worse, they are even more
difficult to write a description of how
you did it and still make it
understandable....
Here is the cookbook method:
1) Turn your Apple //e or //c on and
hit reset to stop the drive.
2) Enter the monitor by typing:
]CALL-151
3) Move the disk controller ROM code to
RAM by typing:
*8600<C600.C700M
*86F9:59 FF
4) Insert your original Dazzle Draw in
drive one and type:
*8600G
5) In a moment, your Apple will beep
and the monitor prompt will appear. Now
type:
*C0E8
*843:59 FF
*86F9:01 08
*8659:50
*8600G
6) The drive will reboot and in a
moment, your Apple will beep and the
monitor prompt will appear. Type:
*COE8
*602B:0F
*843:00 60
*850:40
*F00:8D FC 0F 8E FD 0F 8C FE
*F08:0F BA 8E FF 0F A2 00 BD
*F10:00 00 9D 00 80 E8 D0 F7
*F18:EE 11 0F EE 14 0F AD 11
*F20:0F C9 09 D0 E8 4C 59 FF
*8600G
7) The drive will reboot again and in a
moment, your Apple will beep and the
monitor prompt will appear. Now type:
*C0E8
*FFC.FFF
8) Make a note or the values returned
for the locations $FFC to $FFF.
Remember, $FFC = Accum, $FFD = X-reg,
$FFE = Y-reg, and $FFF = Stack Pointer.
9) Disable the configuration save
option by typing:
*75C5:A7 7B
10) Boot a normal DOS 48K slave disk
and save the memory pieces by typing:
*C600G
(boots disk)
]BSAVE DD,A$6000,L$2900
11) Type in this program at $5EFD by
typing:
]CALL-151
*5EFD:20 2A 5F AD E9 C0 A2 00 BD 00 80
*5F08:9D 00 00 E8 D0 F7 EE 07
*5F10:5F EE 0A 5F AD 07 5F C9
*5F18:89 D0 E8 A2 FF 9A A0 00
*5F20:A2 60 AD 10 C0 A9 BA 4C
*5F28:00 64 20 58 FC 20 9A 61
*5F30:AD 10 C0 AD 00 C0 10 FB 60
12) Now you can enter the values you
wrote down for the 4 registers. Do this
by typing:
*5F26:xx (xx = value for Accumulator)
*5F21:xx (xx = value for the
X-register)
*5F1F:xx (xx = value for the
Y-register)
*5F1C:xx (xx = value for the Stack
Pointer)
13) Save the whole Dazzle Draw startup
program by typing:
*BSAVE DAZZLE.START,A$5EFD,L$2A03
14) Put your DOS 3.3 System Master in
the drive and type:
*RUN COPYA
15) After the drive stops and COPYA is
loaded and ready to accept drive and
slot inputs, press:
CTRL
C
(simultaneously)
16) You should now be in BASIC with the
BASIC prompt. Now type:
]CALL-151
*B942:18
*302:1F
*35F:1F
*3D0G
]70
]RUN
17) Now copy the original Dazzle Draw
disk to a blank disk as you would
normally do with COPYA.
18) Write protect the COPYA copy of
Dazzle Draw.
Now to run Dazzle Draw, boot normal DOS
and type:
]BRUN DAZZLE.START
After the drive stops and the text page
clears, put your write-protected COPYA
Dazzle draw in the drive and hit any
key. Dazzle Draw should work normally
from here on.
You may make as many copies of the
COPYA Dazzle Draw disks and of the
DAZZLE.START program as you wish, using
COPYA and FID, respectively.
For the perfectionist or the
experienced Apple user, you may put the
DAZZLE.START program on the COPYA
Dazzle Draw disk and make it a self
booting disk. I am not going to explain
how, but there is room on the disk
since tracks $1E to $22 are completely
empty. BUT BE CAREFUL, as you will have
to use some ingenuity to do it
correctly.
Dazzle Draw uses a slightly modified
ProDOS, and you cannot disturb track 0,
sectors $1 and $7 to $E, since this is
where the ProDOS/Dazzle Draw directory
is. If track 0, sector 1 is changed,
Dazzle Draw will not be able to find
the HELP files from within the program.
Just a note and some food for
thought...
-the Disk Jockey-
Retour sommaire
09) STONEWARE.
Deprotecting Stoneware's DB Master
Version 4.2 and Business Writer.
Requirements:
-Apple II, II+, //e or //c with at
least 64k (required by program).
-At least one DOS 3.3 disk drive.
-COPYA from the DOS 3.3 System Master.
-A sector editor.
-Some blank disks.
-DB Master version 4.2 and/or Business
Writer from Stoneware.
OK, its about time someone put to paper
the deprotection method used for the
Stoneware Series of software! If you
have used (the infamous) DB Master, you
will know EXACTLY what I mean...
The protection used on DB Master
Vertsion 4.2 and Business Writer are
EXACTLY the same. This should be no
great shock since the protection used
is good, and for quite some time
remained untouched by prying eyes. The
main protection used is half tracking,
and Stoneware was one of the first (if
not THE first) publisher to use half
tracking.
--> Note that your original disk will
have to be in perfect condition for
this to work correctly. I had problems
with my Business Writer disk using one
of the Stoneware original disks, but it
worked fine with the other original
backup. <--
So here is the cookbook method:
1) Boot your DOS 3.3 System Master and
when the BASIC prompt appears, type:
]RUN COPYA
2) After COPYA is loaded and asking for
slot specifications, type:
CTRL C
3) You should see the BASIC prompt.
Type:
]CALL-151
*B988:18 60
*B925:18 60
*302:06
*35F:06
*3D0G
]70
]RUN
4) Copy your original DB Master or
Business Writer disk to a blank disk.
5) Re-boot your DOS 3.3 System Master
and when the BASIC prompt appears type:
]RUN COPYA
6) After COPYA is loaded and is asking
for slot specifications, type:
CTRL C
7) You should see the BASIC prompt. Now
type:
]CALL-151
*B988:18 60
*B925:18 60
*3A1:18
*2B0:A9 05 8D D1 02 8D D2 02 60
*2DC:20 B0 02 A9 FF
*2E6:F8
*280:86 2B 85 2A C9 0C 90 02
*288:E6 2A AD 78 04 C9 0C 90
*290:03 EE 78 04 A5 2A 60
*3D0G
]DEL 246,250
]DEL 0,70
]197 POKE 47520,32: POKE 47521,128:
POKE 47522,2: POKE 47523,234
]258 POKE 47520,134: POKE 47521,43:
POKE 47522,133: POKE 47523,42
]RUN
8) Copy the original DB Master or
Business Writer disk to the previously
copied to disk.
9) Reboot normal DOS 3.3 and run your
favorite sector editor and make the
following changes to your COPYA copy:
Track 0, sector 3
byte $88 from $A8 to $18
byte $89 from $D0 to $60
byte $25 from $BC to $18
byte $26 from $8C to $60
Track 0, sector $C
byte $E3 from $C9 to $60
Track 5, sector $A
byte $13 from $C9 to $60
(--> Business Writer only <--).
10) Write the sectors back out.
11) If you are deprotecting DB Master,
repeat the above steps for the second
side of the disk.
And you're all done!
-The Disk Jockey-
Retour sommaire
10) SSI'S RDOS.
Deprotecting SSI's RDOS protection
scheme. By the Disk Jockey.
Requirements:
-A DOS 3.2 System Master.
-The file "RDOS 3.3".
-A blank disk.
-COPYB.
-A sector editor.
-A disk search utility.
-Any SSI original disks.
Several years ago, our good friend
Krakowicz (R.I.P.) wrote an excellent
article on how to deprotect SSI's
protected DOS called RDOS. Recently,
several people have asked me to rewrite
this article, so here it is (once
again, thanks to Krakowicz for all the
help and source code, may he rest in
peace...). Note there are several
excerpts from Krakowicz's original
article here.
RDOS is SSI's protected DOS that they
use in 99% of their releases to date.
This DOS is based loosely on standard
DOS 3.2, the old 13 sector DOS Apple
provided us in February 1979.
But what makes RDOS so difficult to
unprotect is its relationship with
APPLESOFT (most of SSI's programs are
written in APPLESOFT). To be sly, RDOS
is short (lives from $B100-$BFFF). But
worse, RDOS interprets the ampersand
command used liberally throughout the
APPLESOFT programs. The amount of
effort required to deprotect a SSI game
has kept the users at bay.
To get an idea of what you are up
against, boot any SSI game and after a
few moments, reset into the monitor.
Now defeat the autorun BASIC flag by
typing:
*D6:00
And if you reset into the monitor using
a ROM card, turn off the ROM card and
turn on the motherboard ROM by typing:
*C081
(assumes ROM card in slot 0. Add $10
for each slot. For example, if your ROM
card is in slot 3, add $30 to $C081 and
type "C0B1").
Now get into APPLESOFT by typing:
CTRL C
You should now see the APPLESOFT
prompt, and you may type:
]LIST
Ninety-five percent of the SSI programs
use some BASIC code, so you should see
a listing. Notice the use of the
ampersand (&) when ever a DOS command
is to be issued, and notice the DOS
commands are very different from normal
DOS 3.3. Here is a list of commands
that have been found and their DOS 3.3
equivalence:
RDOS DOS 3.3 Function
---- ------- --------
CAT CATALOG catalog the disk.
LOAD LOAD
load a basic file.
RUN
RUN run a basic file.
GOTO EXEC
exec a text file.
SAVE SAVE
save a basic file.
STORE BSAVE save a binary file.
RECALL BLOAD load a binary file.
PRINT WRITE write to a text
file.
READ READ
read from a text file.
END CLOSE
close a text file.
DEL DELETE delete a
file.
NEW
NEW erase basic file
from
memory.
There are more commands, but this is
the most commonly used. Remember, all
these commands must start with an
ampersand (&).
For example, type:
]&CAT
This will give you a RDOS catalog.
Looks a lot different than a DOS 3.3
catalog, doesn't it?
Also, you cannot use all these commands
from the immediate mode. Many must be
executed from within a program to work.
For example, look at the last line of
any of the APPLESOFT programs. You will
see that the last line is really not
part of the program, but is used to
delete the old file and re-save the new
basic program! So if you wanted to
change a basic program, you must make
the changes wanted and then type:
]RUN xxxx
where xxxx is the last line number of
the APPLESOFT program. This will
(generally) delete the old version and
save the new version of the BASIC
program.
To elaborate a little, here is how the
ampersand command works. When the & is
encountered, APPLESOFT jumps to $3F5.
Looking at this location will tell you
that $3F5 contains a JMP $B303.
Examination of this code reveals that
the accumulator is compared to a table
of numbers at $B320-B330, and the
address of the routine to be executed
is picked up from a table in
$B331-B352.
Well, all this is relatively worthless
in our pursuit, which means we must
work through the RDOS RWTS (read -
write - track - sector) and try and
normalize it. On close examination, it
can be seen that the read and write
routines have been lifted almost
verbatim from DOS 3.2, with the address
markers changed to $D4 AA B7 (in most
cases). Note that some particular SSI
games use different address marker, but
the most common is $D4 AA B7. To
normalize this to DOS 3.3 format, we
have to put the appropriate routines in
that will do $D5 AA 96's. The hard part
is that DOS 3.2 uses "6+2" nibblizing
in storing data on the disk, where DOS
3.3 uses "5+3". The end result is that
the pre and post nibblizing routines
must be transplanted from DOS 3.3, and
the read and write byte translate
tables too (if you don't understand
these terms, refer to "Beneath Apple
DOS"). The address markers and the size
of the nibble buffers must also be
adjusted. When this is all done, we end
up with a DOS 3.3 compatible RDOS: RDOS
3.3.
Now we must convert the perverted RDOS
disk to normal DOS 3.3 format. We can
do this using COPYB, and DOS 3.2 RWTS
to read the protected SSI disk. First
we need to make a DOS 3.2 RWTS that
will read the RDOS original disk. The
only change we have to make is to
change the DOS 3.2 address prologue
bytes from $D5 AA B5 to RDOS's format
of $D4 AA B7. This routine is located
at $B975 in DOS 3.2.1, and is probably
the same in DOS 3.2 (I only have the
latest version of DOS 3.2, which is DOS
3.2.1).
So here are the first few steps in the
process of deprotecting an SSI game:
1) Boot DOS 3.2 using your "Basics 3.2"
disk (actually, I am using DOS 3.2.1).
2) After the DOS is loaded, and you
have the APPLESOFT prompt, enter the
monitor, move RWTS down to $8000, and
change the address markers by typing:
]CALL-151
*8000<B700.BFFFM
*8276:D4
*828B:B7
3) Boot a normal DOS 3.3 slave disk and
save the DOS 3.2 RWTS to your COPYB
disk for future reference by typing:
]BSAVE RDOS READ,A$8000,L$8FF
Now for the next trick by RDOS: there
is no sector interleaving in software;
its all done by the sector number
sequencing during RDOS's initialization
routine. DOS uses a lookup table at
$BFA8 to change the sector number read
from the value read off the disk, to
the number it thinks it should be. RDOS
uses an "ascending 7" interleave
scheme, which means that the sequence
of sectors on a disk as read by DOS
3.3's interleave table is:
0,7,E,6,D,5,C,4,B,3,A,2,9,1,B,F.
This may seem complicated, and if you
are confused I suggest you refer to
"Beneath Apple DOS".
Because of this, we must make a few
changes to normal DOS 3.3 RWTS. Then we
can transfer the protected SSI disk to
normal DOS format. Here are the steps
(numbered as a continuation of the
previous steps):
4) Boot normal DOS 3.3 and initialize a
blank disk by typing:
]INIT HELLO
5) Put the disk with COPYB in the drive
and run COPYB by typing:
]RUN COPYB
6) When you are being prompted by
COPYB, press reset and drop into
APPLESOFT.
7) Prepare COPYB to copy the SSI disk
by typing:
]5
]BLOAD RDOS READ,A$8000
]CALL-151
*BE2A:EA EA EA EA
*3D0G
]RUN
8) Now respond to the COPYB prompts as
follows:
13 sector formatting
start track = 1
end track = 34
continue on errors = yes
format disk = no
9) Now you must write the file "RDOS
3.3" onto track 0, sectors 0 to $D.
Reboot DOS 3.3 and bload the RDOS 3.3
file at an even page (such as $800) by
typing:
]BLOAD RDOS 3.3,A$800
and then run your favorite sector
editor (make sure your sector editor
doesn't overwrite the RDOS 3.3 file).
Then copy the RDOS 3.3 file starting
with track 0, sector 0 (buffer $800 in
this case) to your COPYB SSI disk.
Increment the sector and the page
(track 0, sector 1, buffer $900) and
continue to sector $D. Or you can copy
track 0 of any previously kraked SSI
game onto your disk.
You now have a bootable normal OOS
format SSI program. But it will not
work due to some secondary protection.
There are several schemes used to
defeat various copy programs, usually
going under the name "QWERTY". The most
common of these reads in an address
field from track 0, delays a bit, and
looks for an $EE as the next byte on
the track. If it finds it, A $00 is
stored in location $00, otherwise your
computer obnoxiously beeps and the
drive keeps spinning...
This is easy to defeat by changing
bytes $28-29 of the QWERTY file to $A9
00. The best way to do this is to
search the disk for the byte sequence
$49 EE D0, and when you find it change
(starting with) the found $D0 to $A9
00.
There is a similar routine seen only a
few times under a file called @WERTY.
This looks for an $AA following the
address field on any track, and reboots
if it is not found. The remedy here is
to put a $A9 00 at bytes $20-21 in this
file. You can find this file by
searching for the sequence $49 AA D0.
When you find it, change (starting
with) the found $D0 to $A9 00.
Recently, a much more sophisticated
technique has been used (Galactic
Gladiators, Road to Gettysburg) which
does "quarter tracking" or "spiral
tracking". This version of QWERTY reads
in four pages of sequential bytes from
each of the four adjacent half-tracks
from $20.5 to $22.0, storing them at
$1000-1FFF. The three bytes following
the four pages worth of data are used
as the address marker for the data on
the next half-track. This approach
defeats most copiers which write an
entire track and obliterate data on any
adjacent half-track.
After reading in the data, the memory
values are Exclusive-ORed with the
address ($1000 contains $00, $1001
contains $01, etc.), and if an error is
found, it reboots the disk. Placing an
RTS ($60) at the beginning of the
@WERTY file (the entry point is $A0F0)
will avoid the entire issue and make
your COPYA version run.
The final issue in unprotecting the SSI
program at hand is the format of the
saved game disk. We must change the
file that creates a saved game disk so
that is uses a normal DOS format. This
file is called SSI.INIT and loads in at
$800-AFF (it is usually accessed by a
CALL 2800 via APPLESOFT). Since it only
writes address fields, and not data
sectors, it is a very fast init.
All that is necessary to create a
compatible RDOS 3.3 save game disk is
to replace the $D4 AA B7 (or $D5 AA B5)
address marker bytes with $D5 AA 96. To
do this search your disk for $A9 D4 20
CC 09. When you find it change the
found $D4 to a $D5, and change the
found $B7 to a $96. It should be bytes
$F5 and $FF of the sector.
If your disk searches are unsuccessful,
you must find where the QWERTY or
SSI.INIT file lives on the disk, so you
can make the appropriate byte changes
provided above. Refer to Appendix A of
this article on RDOS file structures
and how to decifer the catalog track.
You should now have an unprotected,
normal DOS 3.3 formatted SSI game.
---------------------------------------
APPENDIX A:
There is one additional topic I should
discuss about RDOS, and that is how
files are stored on disk. This might
help you find the track and sector
location of a particular file (such
SSI.INIT or QWERTY). You may or may not
need this information to deprotect your
particular SSI game, depending on how
successful your disk searches were...
RDOS uses track 1 for its catalog
track, and the starting sector is
sector 0, then sector 7, and then
sector 6. Load track 1, sector 0 of
your unprotected SSI game using a
sector editor. Here is what you should
see (assuming you are using the
Inspector):
TRACK 01 SECTOR 0
SLOT 6 DRIVE 1
BUFFER 0800 DOS 16
2BCC
=======================================
0 1 2 3 4 5 6 7 8 9
A B C D E F
-------------------------------------
00- R D O S 2 .
1 C O P Y R I G
10- H T 1 9 8
1 B 1A0010 001A0000
20- S Y S T E M B O O
T
30-
T 0100B1 00011A00
40- S S I . I N I
T
50-
/
B 030008 00031B00
/
/ \/
\/ \/
/
/
/ / first
/
File Type
/ / block
Program A, B,
T
/ number
Name
/
of
starting
blocks
location
The starting track and sector is equal
to the first block (in decimal) divided
by 13, with the remainder being the
sector number. So block $1A00 is equal
to $001A or decimal 26, or track 2,
sector 0. Got that?
That might help you locate some files
on the disk. Good luck in your pursuit
of deprotecting SSI's RDOS!
---------------------------------------
APPENDIX B:
You will notice a difference between
your original SSI disk and your
unprotected version: speed. Your
unprotected program will load slower
because of the sector interleave used
by SSI. The disk must make almost an
additional revolution for each sector
read in.
The easiest way to fix this is to use
"BAG OF TRICKS" and change the sector
skewing to "ascending 01" for all of
the tracks. This will make the load
fast. Note that if you copy the
re-skewed disk with COPYA, the new copy
will have standard sector skewing, and
will have to be re-skewed by Bag of
Tricks to load fast.
-The Disk Jockey-
Retour sommaire
11) SAMMY LIGHTFOOT.
Message by Dr. D-Code.
Cracking Sammy Lightfoot
------------------------
Sammy Lightfoot is unprotected except
for a nibble count. You may use COPYA
to copy the original. Here are the
steps:
1) Copy the original Sammy disk with
COPYA.
2) Run a sector editor and make the
following changes:
track D, sector 0, byte $9B
from $20 00 09
to $EA EA
EA
Don't forget to write the sector back
out to the COPYA copy!
Dr. D-Code!
Retour sommaire
12) MARIO BROS.
MSG LEFT BY: THE THIEF
SCANNER HERE,
TO CRACK MARIO BROS. JUST USE DEMUFFIN
PLUS.
GAME IS AWSOME.
--------------
Retour sommaire
13) 'THE QUEST' CRACK.
MSG LEFT BY: NILE DAVIS
THIS CRACK IS A FAIRLY EASY ONE. FIRST, YOU NEED A COPY OF
NIBBLES AWAY II
(WHICH BY THE WAY IS ONE OF THE GREATEST NIBBLE COPIERS).
SIDE 1: SYNC SIZE: 09
TRKS 0-22: ADDR. D5 AA 96
SIDE 2: SYNC SIZE: 03
(BOOT SIDE) EVEN TRKS:ADDR. D5 AA 96
ODD TRKS: ADDR. D4 AA 96
THAT'S IT. YOUR COPY SHOULD WORK FINE.
NILE DAVIS
/EX
Retour sommaire
14) PEACHTREE.
Kraking Peachtree's "Back to Basics"
Accounting System. By the Disk Jockey.
Requirements:
-Apple //e, //c with at least one disk
drive and DOS 3.3.
-An 80 column card (required by
Peachtree).
-A sector editor.
-Back to Basics from Peachtree
Software.
Kraking the accounting system is fair-
ly easy:
Make a
COPYA copy of one of the sides of the
accounting system, boot the disk. After
the program has loaded and it is just
sitting there spinning the disk drive,
open the disk drive door and put the
original disk in. Notice the program
immediately rewards you by stopping the
drive and continues with the program's
main menu.
So all we need to do is to defeat this
nasty routine, and we have deprotected
the accounting system (yes, we have to
do this for all three disks
If you have a Replay II card, this can
be most handy in locating the offending
code. Simply make a COPYA copy, boot
the copy, and when the program hangs,
press the Replay II button. Now enter
the Replay II monitor, and write down
the location of the Program Counter.
This is the current address being
executed. Finally, reset into the
monitor and examine the code there!
As you can see, the code seeks
the read/write head of the disk drive
to track zero. Next it reads the disk
and compares a byte to the contents of
location $8CEB. If the byte read from
the disk and location $8CEB are not the
same, it goes back to the beginning of
the routine and starts over. Hence that
is why our COPYA copy hangs and keeps
spinning the drive.
So to defeat this routine, we can
insert at $8D1B a JMP (jump to) $8D25,
which by passes the whole read and
check routine. You may try this to see
if it works by typing:
*8D1B:4C 25 8D
*8CF7G
and sure enough, the main menu jumps up
on the screen!
So all that is left to do is to find
this code on the disk and use a sector
editor to change it.
The other two disks use the exact same
protection code, but as different
locations. You may use the same methods
to find the offending code as I just
described above.
Here are the steps:
1) Boot your DOS 3.3 System Master and
type:
]RUN COPYA
2) Copy all three sides of the
Peachtree Accounting System to three
blank disks.
3) Run your sector editor and make the
following changes to the COPYA version
of the disks:
General Ledger:
---------------
Track $13, Sector 0, Byte $AA
change from $10 FB D9
to $4C 25 8D
Accounts Receivable:
--------------------
Track $12, Sector $C, Byte $A9
change from $10 FB D9
to $4C 95 7F
Accounts Payable:
-----------------
Track $13, Sector 8, Byte $A1
change from $10 FB D9
to $4C D6 82
4) Write the sector back out and your
all done!
-The Disk Jockey-
Retour sommaire
15) STANDING STONES.
MSG LEFT BY: SHANE GRUNDY
IF YOU HAVE BEEN HAVING PROBLEMS
COPING STANDING STONES(ELECTRONIC ARTS)
THIS IS FOR YOU.
1)COPY WITH COPYA(IGNORE"UNABLE TO
READ"SIGNAL.
2)NOW USE A SECTOR EDITOR AND MAKE THE
FOLLOWING CHANGES:
TK
SEC BYTE
FROM TO
--------------------------------------
11
04
44
20 EA
"
"
45
D9 EA
"
"
46
03 EA
"
"
47
20 EA
"
"
48
00 EA
"
"
49
0D EA
YOUR COPY SHOULD WORK.AND IT CAN
NOW BE COPIED BY ANY NIBBLE COPIER.
Retour sommaire
16) DESIGNWARE.
Deprotecting Designware Programs. By
the Disk Jockey.
Requirements:
-Apple II, II+, //c, //e.
-A sector editor.
-Any Designware program.
Designware has used the same protection
on all of its recent releases. I used
"Spellicopter" and "States and Traits"
for an example, but this procedure
should work on all of Designware's
recent releases.
1) Boot your DOS 3.3 System Master and
run COPYA by typing:
]RUN COPYA
2) Copy the Designware program to a
blank disk.
3) Now run your sector editor and make
the following change to the copied
disk:
Track 0, sector 5, Byte $39:
Change from $00 $BB
to $93 $B7
4) Write the sector back out to disk.
And you're all done!
-the Disk Jockey-
Retour sommaire
17) CRACK MURDER BY THE DOZEN.
MSG LEFT BY: THE THIEF
THIS IS A QUITE SIMPLE PROGRAM TO CRACK
FOR IT ALREADY HAS A CATALOG WHICH YOU
CAN GET INTO, BUT IF YOU TRY FID OR
SOMETHING LIKE THAT BOOM.... CRASH....
ANY HOW HERE'S WA'CA DO.
=======================================
1. CALL-151
2. B942:18
6. B925:18 60
7. B988:18 60
8. B9BD:ED DA
9. BRUN FID
=======================================
Retour sommaire
18) EASY COM/EASY GO.
Deprotecting Easy Com/Easy Go from
Transcend Software. By the Disk Jockey.
Requirements:
-Apple II+, //e or //c with 64K of RAM.
-At least one DOS 3.3 Disk Drive.
-A sector editor.
-2 blank disks.
-Easy Com/Easy Go from Transcend.
Easy Com/Easy Go copies straight with
COPYA - no parameter changes necessary.
Of course, as you would expect, the
COPYA copy does not work...
After booting the COPYA copy, the
program starts to load just as the
original. After ProDOS is done loading
and we see the ProDOS welcome message,
we hear a few more tracks being read
in. Then there is a pause, and BEEP!
The program dumps us into the monitor
with the contents of the registers
displayed just after an address of
$209F.
The first part ($2067-2077) wipes out
memory from $1E00 to $1FFF with the
value $00. The second part ($2078-208C)
wipes out memory from $2100 to $BFFF.
Finally, the third part ($2095-20A1)
wipes-out memory from $2000-20FF. But
in the process it starts wiping out
itself, and hence the program bombs at
$209D when the store command starts
storing the byte $00 over its own
instruction.
So we only have to NOP (no instruction)
the two BNE $2067 instructions and the
BVS $2067 instruction at $204F, $2056,
and $205B, respectively. They didn't
bother EORing this routine
($204C-205D), so we can use a disk
search utility to find the routine at
track 1, sector $D.
That is all the protection we have to
defeat. So to deprotect Easy Com/Easy
Go in Cookbook form:
1) Boot your DOS 3.3 System Master and
at the BASIC prompt, type:
]RUN COPYA
2) Copy the original Easy Com/Easy Go
disk (both sides) to a blank disk(s).
3) Exit COPYA and run your favorite
sector editor.
4) Make the following byte changes to
side 1 of your COPYA copy of Easy
Com/Easy Go:
Track 1, sector $D
byte $4F from $D0 16 to $EA EA
byte $56 from $D0 0F to $EA EA
byte $5B from $70 0A to $EA EA
5) Write the sector back out to side 1
of your COPYA copy of Easy Com/Easy Go.
And you're all done!
If you want to defeat the nibble count
routine anyway, here is what you must
do. It is not necessary to defeat the
nibble count for the program to work,
but it will make the loading time
slightly faster.
Read in track $0, sector $1 of side 1
and make the following changes:
byte $76 from $AC 96 to $96 96
byte $80 from $AC 8E to $96 96
byte $8A from $AC 94 to $96 96
byte $95 from $AC A1 to $96 96
byte $AE from $AC 00 to $96 96
byte $BD from $AC 8F to $96 96
byte $C6 from $AC 8F to $96 96
byte $D0 from $AC 95 to $96 96
byte $DA from $AC A3 to $96 96
Don't forget to write the sector back
out to side 1 of your COPYA copy of
Easy Com/Easy GO. This will make the
program load slightly faster.
One additional note: You may have to
take your modem out of your computer
and then configure Easy Com/Easy Go for
your modem. I had problems running my
copy until I configured Easy Com/Easy
Go without my modem installed! After I
had it configured correctly, I put my
modem back in and it worked perfectly.
-the Disk Jockey-
Retour sommaire
19) ADVENTURE WRITER.
Deprotecting Adventure Writer from
Codewriter Software. By the Disk
Jockey.
Requirements:
-Apple II, II+, //e with at least one
DOS 3.3 disk drive.
-A sector editor
-COPYA from the DOS 3.3 System Master.
-A blank disk.
-Adventure Writer.
1) Boot your DOS 3.3 System Master
disk.
2) Run COPYA by typing:
]RUN COPYA
3) After the drive stops, and COPYA is
loaded, exit into BASIC ty typing:
CTRL C
4) Enter the monitor and disable the
"UNABLE TO READ" error and tell COPYA
to stop reading at track 16 ($10). To
do this type:
]CALL-151
*3A1:18
*302:11
*35F:11
*B942:18
*3D0G
5) Make the following changes to COPYA
to read the protected disk. Type:
]197 POKE 47445,165: POKE 47455,219:
POKE 47466,189: POKE 47505,231:
POKE 47515,153: POKE 47335,146:
POKE 47345,148: POKE 47356,205:
POKE 47413,229: POKE 47423,167
]247 GOSUB 400
]257 GOSUB 400
]400 POKE 47445,213: POKE 47455,170:
POKE 47466,150: POKE 47505,222:
POKE 47515,170: POKE 47335,213:
POKE 47345,170: POKE 47356,173:
POKE 47413,222: POKE
47423,170
]410 RETURN
]70
(delete line 70)
]RUN
6) Now copy your original Adventure
Writer to a blank disk. When first
copying, the drive will recalabrate 20
times. Ignore this and let the copy
finish.
7) Reboot normal DOS and enter the
monitor and defeat the DOS error
checking routine by typing:
*B942:18
8) Run your favorite sector editor and
copy track 0, sectors 0 to 9 from the
original disk to your COPYA Copy.
9) Reboot normal DOS again, and re-run
your favorite sector editor.
10) Make the following changes to your
COPYA version of Adventure Writer:
Track 0, sector 2:
byte $53 from 92 to D5
byte $58 from 94 to CD
byte $5D from CD to AD
byte $E7 from 92 to D5
byte $F1 from 94 to AA
byte $FC from CD to AD
Track 0, sector 3:
byte $55 from A5 to D5
byte $5F from DB to AA
byte $6A from BD to 96
byte $42 from 38 to 18
Track $0B, sector $F:
byte $B3 from D0 E6 to EA EA
byte $BC from D0 DD to EA EA
byte $EE from D0 0A to EA EA
byte $FA from 38 to 18
byte $DA from 8D 3F 70 to EA EA EA
byte $CB from 8D 3E 70 to EA EA EA
byte $9B from C9 C4 F0 0D EE 29 0E D0
F2 EE 2A 0E D0
to A9 99 8D 3E 70 A9 CD 8D
3F 70 4C A8 0D
11) Make sure you write the sectors
back out to disk after you edit them.
And you're all done!
-the Disk Jockey-
Retour sommaire
20) PATTERN MAKER.
Deprotecting Pattern Maker from
Scarborough Systems. By the Disk
Jockey.
Requirements:
-Apple II, II+, //e or //c with at
least 64K of RAM.
-At least one DOS 3.3 disk drive.
-COPYA from the DOS 3.3 System Master.
-A sector editor.
-A blank disk.
-Pattern Maker from Scarborough
Systems.
1) Boot your DOS 3.3 System Master
disk.
2) Run COPYA by typing:
]RUN COPYA
3) After the drive stops and COPYA is
asking from slot and drive choices,
press:
CTRL C
4) You should now be in BASIC. To copy
only tracks 0 to 2 type:
]CALL-151
*35F:03
*302:03
*3D0G
]70
]RUN
5) Copy the original Pattern Maker disk
to a blank disk.
6) Reboot your DOS 3.3 System Master
disk.
7) Run COPYA by typing:
]RUN COPYA
8) After the drive stops and COPYA is
asking from slot and drive choices,
press:
CTRL C
9) You should now be in BASIC. To copy
track 3 to $22 type:
]CALL-151
*2B0:A9 02 8D D1 02 8D D2 02 60
*2DC:20 B0 02 A9 FF
*2E6:F8
*3D0G
]197 POKE 47445,215: POKE 47335,215:
POKE 47413,223
]258 POKE 47445,213: POKE 47335,213:
POKE 47413,222
]DEL 246,250
]70
]RUN
10) Copy the original Pattern Maker
disk to the disk you copied track 0 to
2 previously.
11) Reboot normal DOS and run your
favorite sector editor.
12) Make the following changes to the
COPYA copy of Pattern Maker using your
sector editor:
Track 0, sector $F
byte $42 from $38 to $18
Track 0, sector $D
byte $6B from $D7 to $D5
13) Write the sector back out to your
COPYA copy of Pattern Maker.
And you're all done!
-the Disk Jockey-
Retour sommaire
21) BANK STREET WRITER //C.
Deprotecting Bank Street Writer IIc/e
by Broderbund Software.
Requirements:
-Apple //e or //c with 128k (required
by program).
-At least one DOS 3.3 disk drive.
-COPYA from the DOS 3.3 System Master
disk.
-A sector editor.
-A blank disk.
-A blank initialized 48k DOS 3.3 slave
disk.
-Bank Street Writer IIc/e.
Although Bank Street Writer looks easy
enough, deprotecting it was not an easy
chore. The bulk of their protection was
changing the address and data marker
from normal DOS's.
Track 1 to $22 are protected by
changing the address and data markers
from normal DOS's to $A5 96 BF and $D4
D5 D6, respectively. Track 0 is
protected with different address and
data markers than DOS or even tracks 1
to $22 (but we'll worry about that
later). Converting this format to
normal DOS only requires adding several
lines to COPYA, and copying tracks 1 to
$22.
I had a good deal of difficulty
figuring out what was on track 0, but
figured the best (and easiest) way was
to do some minor boot-code tracing.
1) Boot your DOS 3.3 System Master and
type:
]RUN COPYA
2) Now exit into BASIC by typing:
CTRL C
3) Now type in the following changes to
COPYA:
197 POKE 47445,165: POKE 47455,150:
POKE 47466,191: POKE 47335,212:
POKE 47345,213: POKE 47356,214
248 POKE 47445,213: POKE 47455,170:
POKE 47466,150: POKE 47335,213:
POKE 47345,170: POKE 47356,173
258 POKE 47445,213: POKE 47455,170:
POKE 47466,150: POKE 47335,213:
POKE 47345,170: POKE 47356,173
4) Change the COPYA code so it only
copies tracks 1 to $22, and ignores the
address and data epilogue bytes. Type:
]DEL 0,70
]CALL -151
*B942:18
*2B0:A9 00 8D D1 02 8D D2 02 60
*2DC:20 B0 02 A9 FF
*2E6:F8
*3D0G
]RUN
5) Copy the original Bank Street Writer
//c disk to a blank disk.
6) Re-boot normal DOS 3.3
7) Enter the monitor to do some
boot-code tracing. Type:
*8600<C600.C700M
*86F8:4C 59 FF
9) Put the original Bank Street Writer
//c disk in drive 1 and type:
*8600G
10) Now finish the trace by typing:
*820:4C 59 FF
*86F8:4C 01 08
*8659:80
*8600G
*C0E8
11) Track 0 will be read in. Save this
to disk by putting an initialized DOS
3.3 disk in the drive and typing:
*14D7:18 18
*1449:D5
*1453:AA
*145D:AD
*152E:D5
*1538:AA
*1543:96
*151B:18
*156B:EA EA
*9D84G
]BSAVE BSW1,A$1400,L$700
12) Get your sector editor out and
write the following pages of the BSW1
file to the appropriate tracks and
sectors of the COPYA Bank Street Writer
//c disk:
$1400-14FF track 0, sector 1
$1500-15FF track 0, sector 2
$1600-16FF track 0, sector 3
$1700-17FF track 0, sector 4
$1800-18FF track 0, sector 5
$1900-19FF track 0, sector 6
$1A00-1AFF track 0, sector 7
13) Read in track 0, sector 0 of a DOS
48k slave disk at $800-8FF with a
sector editor and enter the following
code:
*84A:4C 80 08
*880:20 58 FC 8D F3 03 8D F4
*888:03 A2 00 BD 00 B7 9D 00
*890:14 E8 D0 F7 EE 8D 08 EE
*898:90 08 AD 90 08 C9 1B D0
*8A0:E8 4C 00 14
14) Write this code back to track 0,
sector 0 of the COPYA copy of the Bank
Street Writer //c disk.
15) Edit track 4, sector 7 bytes $7E to
$85:
from D4 D5 D6 D7 A5 96 BF 9A
to D5 AA AD DE D5 AA 96 DE
and write the sector back out.
And you're all done!
-The Disk Jockey-
Retour sommaire
22) CRACK MICKEY'S SPACE ADV.
MSG LEFT BY: RESET VECTOR
This is a new Sierra Online program that is protected with their usual
track 0
nibble count, and it cracks in about 5 minutes with a technique I have
previously documented.
When the drive goes to check track 0 (I use a Trak Star, or you can
open your
drive or just listen for the sweep at the very end of the boot), hit
the
switch on your NMI board and check the program counter. You
will find that
the PC is at about $1580 or somewhere like that. So what you
have to do is
search the disk (it is normally formatted) for a JSR into the $1500
region.
The only program that will do this is the TRACER from the CIA
Files. Just
search for the wildcard, 20==15. You will find such JSR's in
4 or 5 locations
on the disk; just try putting EA EA EA in place of this code until you
find
the crack that works. In this case it is on track 18 sector
E, change bytes
18-1A to EA EA EA .
This exact same technique works for the other new ONLINE release,
Winnie the
Pooh, but the code is in the $A00 range. I lost the paper
with the sectmod
on it so I can't tell you exactly, but it shouldn't take long to find.
Courtesy of ->Reset Vector!
Retour sommaire
23) KRACK PANDORAS BOX.
MSG LEFT BY: PARITY ERROR
RUN COPYA
CONTROL C
70
CALL-151
B992:EA EA
B991:DF
BCAE:DF
BC60:FE
3D0G
RUN
COPYA IT AND EDIT THE FOLLOWING:
TRACK 0 SECTOR 3 BYTE 91 FROM DF TO DE
TRACK 0 SECTOR 6 BYTE AE FORM DF TO DE
TRACK 0 SECTOR 6 BYTE 60 FROM FE TO FF
LATER
***PARITY ERROR***
Retour sommaire
24) SENSIBLE SPELLER PRO.
MSG LEFT BY: PARITY ERROR
TO KRACK THE NEW PRODOS SENSIBLE SPELLE
R:
COPYA THE DISK (IT COPIES BUT WILL NOT
BOOT DUE TO A NIBBLE COUNT)
EDIT TRACK A SECTOR E BYTES 57 AND 58
FROM BD 8C TO 18 60.
THATS IT.
NOTE-MOST PRODOS DISKS SEEM TO BE
EITHER TOTALLY UNPROTECTED,OR IN
COPYA FORMAT WITH A NIBBLECOUNT.
LATER
***PARITY ERROR***
Retour sommaire
25) KRACK MICRO LEAGUE.
MSG LEFT BY: PARITY ERROR
BLOAD DEMUFFIN PLUS,A$6803
BOOT YOUR COPY OF MICRO LEAGUE
CNTRL C AT PROMPT
CALL-151
803<6803.9000M
803G
CONVERT ALL FILES
THATS IT!
NOTE-ON THIS AND MANY OLD GAMES
YOU CAN CATALOG THE DISK FROM THE
MONITOR BY A56EG.ON MOST GAMES WHERE
THIS IS POSSBIBLE,IT IS A GOOD IDEA
TO TRY DEMUFFIN PLUS,EITHER THE WAY
I DID ABOVE,OR BY SOME OTHER METHOD.
LATER
***PARITY ERROR***
Retour sommaire
26) CALCULUS TOOL KIT.
MSG LEFT BY: PARITY ERROR
THIS ONE COPIES WITH COPYA BUT WILL
NOT BOOT.
TO KRACK IT,BOOT UP NIBBLES AWAY II
OR ANY OTHER EDITOR AND LOOK ON
TRACK 12 SECTOR D.ON ONE PLACE IN
THIS SECTOR (I DONT REMEMBER THE EXACT
BYTES THIS TIME) YOU WILL FIND A DISK
ACCESS (BD 89 C0) THAT IS NOT SUPPOSED
TO BE THERE. PUT AN 18 60 IN ITS PLACE.
IT SHOULD NOW BE DONE.THE DISK IS
CATALOGABLE.
LATER
***PARITY ERROR***
Retour sommaire
27) THE MISSING RING.
MSG LEFT BY: PARITY ERROR
TO KRACK THE MISSING RING (BY DATAMOST)
JUST:
RUN COPYA
CNTRL C
70
CALL-151
B942:18
3D0G
RUN
EDIT TRACK 0 SECTOR 3 BYTE 42 TO AN 18
THEY CHANGED ONLY THE EPILOGS AND SYNC
BYTES IN RWTS.
LATER
***PARITY ERROR***
L.S.D.
Retour sommaire
28) CAVERNS OF FREITAG.
MSG LEFT BY: PARITY ERROR
BLOAD DEMUFFIN PLUS,A$6803
BOOT DISK
CNTRL C
CALL-151
803<6803.9000M
803G
CONVERT ALL FILES
THATS IT!
NOTE-THIS WORKS ON MOST OF THE OLD AND
THE NEW MUSE GAMES.
LATER DUDES----
***PARITY ERROR***
Retour sommaire
29) COVETED MIRROR.
MSG LEFT BY: JIM MITCHELL
WELL, HERE IS A WAY TO CRACK THE COVETE
D MIRROR.
RUN COPYA
CTRL RESET
]70 (DELETE LINE 70)
]CALL-151 (ENTER MONITOR)
B942:18 60
B954:29 00
B990:29 00
B934:29 00
3D0G (RETURN TO APPLESOFT)
]RUN
COPYA BOTH SIDES. SECTOR EDIT SIDE 2
TK 0 SEC 3
BYTE
FROM TO
35
DA DE
42
38 18
91
DA DE
54:C9 D5 D0 F0 EA
THAT SHOULD DO IT.
JIM MITCHELL
Retour sommaire
30) CRACK TREASURE HUNTER.
MSG LEFT BY: ONE EYE
SO YOU WANNA BE A D.J.? WHAT MUST YOU
DO TO BE A D.J.?
CRACK T.H. IN A COUPLE OF EASY STEPS
1. BOOT DISK WAIT FOR ']' THEN HIT
CTRL-C
2. TYPE 'CALL-151' THEN TYPE '4000<B800
.BFFFM' THIS RELOCATES RWTS AT A
USEABLE PLACE IN MEMORY
3. BOOT SLAVE DISK AND TYPE 'BSAVE RWTS
,A$4000,L$800'
4. BOOT ADVANCED DEMUFFIN AND LOAD NEW
RWTS MODULE AT B8. THE COPY DISK
5. BOOT SECTOR EDITOR AND CHANGE THE
FOLLOWING
T-1 S-7 BY-00-01
TO: 38 60
THAT SHOULD DO IT
LATER
ONE EYE/1200 CLUB
Retour sommaire